Engineering & Technology
Deep learning Networks
Smart Intelligent Intrusion Detection Systems (IDS): How to build a Deep learning Networks based IDS
September 05, 2019RESEARCH REPORT
In Brief
- Artificial Intelligence is a recent trend in machine learning, and Deep Learning is a major leap forward in terms of technology
- Deep Learning performs complicated computations, thereby making it suitable for large datasets and big data applications.
- Large Image datasets can make use of Deep Learning effectively. However, it can also be useful for IDS applications.
Simple identification of an object in an image is very simple for even a small kid. While this might be easy for humans, this was extremely difficult for computers. A specific background can be identified through GIS, but identifying specific objects like birds, trees, and animals seemed a tedious task for the computers. While machine learning has been available for some time, it has been limited to certain criteria and could not be utilized for complicated predictions and identifications[Field].
The introduction of Deep learning has been instrumental in advanced capabilities and has taken the field of machine learning a leap forward. It is a type of Artificial Intelligence, where it imitates the process of the human brain for carrying out the computations and generating patterns for making decisions. Hence, it is also known as Deep Neural network. It is an unsupervised learning system where it can learn by creating feedback loops. It is different from conventional neural networks with respect to the number of layers. DNN contains hidden layers that are used for computations.
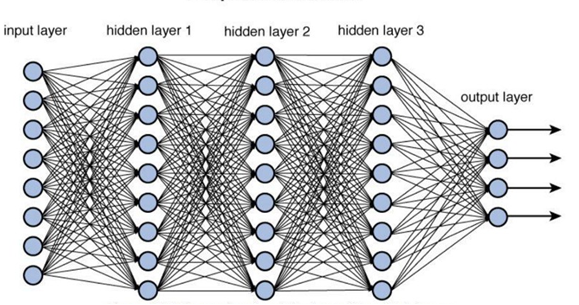
Although it requires computational power, it is not necessary to have a large amount of data with respect to textual data. However, when images are considered, it requires lots of data to the tune of big data. It is highly difficult for a human being to go through this data, and it will take years just to understand and retrieve the data. The introduction of Deep Neural Networks has largely improved the process and has improved the speed of training and classification. Large corporations now use this to collect user data and managing them. It has found itself in a wide range of applications right from image processing to detecting bank frauds over the internet,
Each layer in the neural network builds on the previous layers with additional data related to the considered factors. Each factor may have thousands of data instances, making it extremely difficult for human computations. The Deep network may generate a pattern for each instance. From the different layers, the final layers put these together and give out the final instances. If an Intrusion Detection System (IDS) is taken as an example for implementing the deep network, the features of each attack will involve a hidden layer.
In the previous article, the datasets are discussed, and it is known that there is a presence of unnecessary features in the datasets. These can be removed using feature selection algorithms. With feature selection, unnecessary defunct features will be removed. These features not only remain unnecessary for the classification and training process, rather they affect the performance by reducing the accuracy and increase the classification time. These reduced features each form a hidden layer where they are mapped through each of the individual features of instances. Each instance acts as an input and then passes through the various hidden layers and finally results in two outputs, where it will be classified into attacks or normal traffic. In some datasets, multiclass results are available, and hence each attack is represented by an output. Hence, the number of outputs is not two but depends on the number of attacks
When the training dataset is given to the DNN, the artificial neurons get assigned in such a way that it can solve related solutions. Hence when unlabelled attacks are sent to the classifier, it can be able to identify the attacks with high precision. Due to the higher number of hidden layers, they are able to identify the attacks with higher accuracy.

Summary
Neural networks are sometimes not preferred since they start blankly without any knowledge and then pass through to get accurate models. Since they do not make any assumptions on the functional correlation between input and output, they are considered to be inefficient. However, this is only applicable for very small data. This issue will not be faced in large datasets; hence, this algorithm can be considered whenever large datasets are considered.
- Abusitta, A., Bellaiche, M., Dagenais, M., & Halabi, T. (2019). A deep learning approach for the proactive multi-cloud cooperative intrusion detection system. Future Generation Computer Systems, 98, 308–318. https://doi.org/10.1016/j.future.2019.03.043
- Chiba, Z., Abghour, N., Moussaid, K., El Omri, A., & Rida, M. (2019). Intelligent approach to building a Deep Neural Network-based IDS for cloud environment using a combination of machine learning algorithms. Computers & Security, 86, 291–317. https://doi.org/10.1016/j.cose.2019.06.013
- Chien, J.-T. (2019). Deep Neural Network. In Source Separation and Machine Learning (pp. 259–320). Elsevier. https://doi.org/10.1016/B978-0-12-804566-4.00019-X
- Hodges, C., Bennamoun, M., & Rahmani, H. (2019). Single image dehazing using deep neural networks. Pattern Recognition Letters, 128, 70–77. https://doi.org/10.1016/j.patrec.2019.08.013
- Li, B., & Pi, D. (2019). Learning deep neural networks for node classification. Expert Systems with Applications, 137, 324–334. https://doi.org/10.1016/j.eswa.2019.07.006
- Zhou, D.-X. (2019). The universality of deep convolutional neural networks. Applied and Computational Harmonic Analysis. https://doi.org/10.1016/j.acha.2019.06.004
Related Topics Engineering and Technology
Related Services
- Guidelines to Write a Research Proposal for Neurology Research Scholars - March 19, 2021
- How to Choose a PhD Dissertation Topic For Economic Research? List out the Criteria for Topic Selection - March 11, 2021
- Beginners Guide to Write a Research Proposal for a PhD in Computer Science - February 19, 2021














